Introduction:
In cryptocurrency, several key technologies are fundamental to the development, security, and functionality of blockchain networks and digital assets. Here are the top 5 technologies commonly used in the crypto space:
Use in five technologies
1. Blockchain Technology:
Blockchain Technology is the foundational pillar of the entire cryptocurrency ecosystem. It is a revolutionary technology transforming digital transactions, offering a decentralized, secure, and transparent method for recording and verifying data.
Key Benefits of Blockchain (primary key)
- Security: Blockchain’s cryptographic nature makes it highly secure. The decentralized nature also reduces the risk of fraud or hacking.
- Transparency: All transactions are recorded in a way that is open for anyone on the network to view, making the system transparent.
- Efficiency: Blockchain can eliminate the need for transaction intermediaries, reducing costs and speeding up processes.
- Traceability: Blockchain provides a clear record of ownership and transaction history, which helps track the origin of assets.
` 
2. Smart Contracts (primary key)
Smart Contracts are self-executing agreements with the terms directly written into code. They automatically execute and enforce the terms once predetermined conditions are met, removing the need for intermediaries, reducing costs, and increasing efficiency.
Key Features of Smart Contracts
- Autonomy: Once deployed, intelligent contracts are self-sufficient and can operate without human intervention.
- Security: Smart contracts inherit the security features of the blockchain, making them resistant to tampering or unauthorized change.
- Efficiency: Smart contracts automate contract execution, reducing the time and costs associated with manual processing and third-party involvement.
- Accuracy: The precise nature of code ensures that the terms of the contract are executed exactly as written, reducing the risk of errors or misunderstanding.

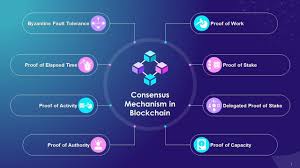
3. Consensus Mechanisms (primary key)
Consensus Mechanisms are critical processes used in blockchain networks to achieve agreement among distributed participants on the blockchain’s state. They ensure that all nodes (computers) in the network agree on the same version of the truth, allowing the blockchain to function as a decentralized and secure ledger. Different blockchain platforms use various consensus mechanisms, each with advantages and trade-offs.
Importance of Consensus Mechanisms
- Security: Consensus mechanisms are vital for a blockchain’s security. They prevent double spending, ensure that transactions are recorded in the correct order, and make it extremely difficult for any single entity to alter the blockchain.
- Decentralization: Consensus mechanisms allow a distributed network of nodes to agree on a single blockchain version without needing a central authority. This decentralization is a crucial feature of blockchain technology.
- Scalability: Different consensus mechanisms offer various levels of scalability, affecting how many transactions a network can process per second. Scalability is crucial for blockchain networks to handle increasing numbers of users and transactions.
4.DeFi Protocols:(secondary key)
DeFi Protocols are blockchain-based financial services that operate without intermediaries. They offer various financial products, such as lending, borrowing, trading, and insurance. DeFi leverages smart contracts to automate these services, making them accessible to anyone with an internet connection. This decentralized approach has the potential to democratize finance by providing financial services to people who may not have access to traditional banking.
Key Features of DeFi Protocols
. No Central Authority: DeFi operates on decentralized blockchain networks, meaning control is distributed across the network rather than concentrated in a single entity. This allows for peer-to-peer transactions without the need for intermediaries.
. Trustless Environment: Users interact directly with smart contracts, eliminating the need to trust a central institution. The code enforces the terms of agreements, ensuring transparency and fairness.

5. Interoperability Protocols (secondary key)
Interoperability protocols ensure that different systems, devices, and software applications can communicate and work together effectively. These protocols define the rules and standards that allow for the exchange of data and functionality between diverse systems, enabling them to interact seamlessly despite differences in technology, architecture, or vendor origin.
Critical Concepts of Interoperability Protocols
- Standardization: Interoperability protocols rely on standardized formats and procedures to ensure system consistency. Standards are often developed by international organizations like the ISO (International Organization for Standardization) or the IEEE (Institute of Electrical and Electronics Engineers).
- Data Exchange: Protocols facilitate data exchange by defining how data is formatted, transmitted, and received between systems. Standard data exchange protocols include HTTP/HTTPS (for web communications), FTP (File Transfer Protocol), and SOAP (Simple Object Access Protocol) for web services.
- Compatibility: Interoperability protocols ensure that systems developed by different manufacturers or developers can work together without requiring significant customization or modification.
- Security: Protocols often include security measures such as encryption, authentication, and authorization to protect the data exchanged between systems and to ensure that only authorized systems and users can interact.

Conclusion:
These individuals have played significant roles in developing blockchain technology, smart contracts, and related protocols. However, the list represents a thematic grouping of concepts rather than a direct reference to a person.
